 CLI spoofing doesn’t have to be as big a problem as it is.
CLI spoofing doesn’t have to be as big a problem as it is.
In the third of this week’s posts on VoIP fraud guest editor David Cargill has Matt Anthony, Vice President of Marketing at Pindrop Security as a contributor.
There was once a time when people trusted the number that showed up on their Caller ID. Phone companies charged extra for the service. Even banks allowed you to activate your credit card just by calling from a registered phone number. Today, that is no longer the case.
Caller ID (CLI) and Automatic Number Identification (ANI) were originally designed as systems to be used internally by the phone companies. As such, they didn’t need any real security. As they emerged as consumer facing tools, they never developed the security features that we expect today.
The result is that spoofing Caller ID data, or ANIs, is very easy. A quick Google search turns up pages of articles on how to spoof a number. App stores are full of easy to use apps that enable spoofing. One smartphone app, Caller ID Faker, has over 1,000,000 downloads.
Adding to the problem is the fact that in general, Calling Liner ID spoofing is completely legal. Though it is always illegal to use CLI spoofing for fraud or threatening messages, it is perfectly legal to spoof a number as a friendly prank, or as a helpful business practice. (Think doctors on call who don’t want to give out their cell phone number.) While it might be fun to spoof a CLI in a prank call to your friend, too often fraudsters are the ones disguising their numbers to hide their criminal activity.
Pindrop Security tracks phone fraud activity and trends. We have found that CLI and ANI spoofing is the most common technique used by phone fraudsters. In addition, more than half of the caller ID spoofing attacks cross international boundaries, meaning they are almost impossible to track down and prosecute.
Consider the case of one attacker, known to Pindrop researchers as “Fritz.” This fraudster is likely based in Europe and works alone. Fritz is in the business of account takeover. He calls financial institution call centres, impersonating legitimate customers by spoofing ANIs, and socially engineers the bank into transferring money out of an account. In one four month period, we found that Fritz had targeted 15 accounts. We estimate that he has netted more than £650,000 a year for at least several years.
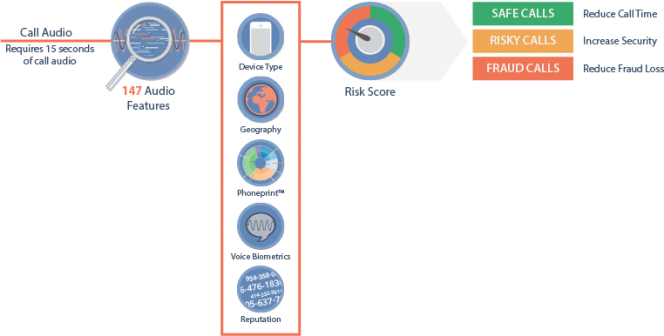
While there is no technology that can prevent CLI spoofing, it is possible to detect these calls. The key is to detect anomalies between the information being sent over the Caller ID and the actual audio characteristics of a call using phoneprintingTM, created by Pindrop Security.
Phoneprinting technology analyses the audio content of a phone call, measuring 147 characteristics of the audio signal in order to form a unique fingerprint for the call. Phoneprinting can identify the region the call originated from and determine if the call was from a landline, cell phone or specific VoIP provider. These pieces of information provide an unprecedented level of insight into caller behavior.
So, if a Caller ID says a call is coming from London, but the phoneprint of the call shows that the individual is calling from 1,000 miles away, it should be a red flag for anyone running a call centre that the caller has malicious intent.
One recent fraud attempt thwarted by Pindrop tools happened on a Saturday night, a time when most call centre employees are not at their most vigilant. The caller asked to transfer £63,900 from one bank to another. The Caller ID matched the phone number associated with the account, and the caller knew all the answers to the identity questions the agent asked. However, while the Caller ID said the call was coming from San Francisco, Pindrop detected that the call was actually coming from a Skype phone in Nigeria. As a result, the wire transfer was put on hold, and the bank was able to verify with the account holder that the request was fraudulent.
Pindrop phoneprinting solutions are already protecting calls to top banks, financial institutions, and retailers. The Pindrop platform is a comprehensive solution designed to protect the entire call system: inbound, outbound, live, recorded and in the IVR, customer-facing and employee-facing interactions. Pindrop uses the information from the phoneprint to create a highly accurate and highly actionable risk score for each call, which has allowed it to catch more than 80 percent of fraud calls within 30 seconds after the call has been initiated.
Historically, the phone channel has been over-trusted and under-protected, making it a major target for fraudster exploitation. Today, technology is available to detect spoofing and stop phone fraud.
Matt Anthony, Vice President of Marketing
www.pindropsecurity.com
Matt Anthony is the Vice President of Marketing at Pindrop Security. With over twenty years of experience in the technology industry, Matt is a frequent speaker at technical conferences. Prior to joining Pindrop, Matt served as Director of Marketing at Dell SecureWorks. Matt has also held marketing roles at CipherTrust, Monorail, and Dell Computer. He is a graduate of the University of Texas at Austin.
Check out our other VoIP fraud posts here. Below are links to other fraud related posts this week:
PABX fraud by Manuel Basilavecchia here
IRSF Fraud by Colin Yates here
One reply on “Caller ID Is Broken – How Can We Fix It?”
The first requirement to make CallerID more useful is surely to get everyone using it – I can’t ignore Withheld or Unavailable calls if they might be from the Doctor, School, Hospital etc and urgent.
We need a valid return call ID to be presented on all calls from commercial or official bodies, and I am wary that security improvements may make that more difficult.