Telecoms and IT security in the UK and Technical best practice
In an excellent and wide ranging two part series, SIP Trunk Plus CEO Jonathan Rodwell dives into the world of telecom fraud. In this first post he looks at Telecoms and IT security in the UK and Technical best practice.
Executive Summary
Telecoms and IT security is a massive industry in 2015, but the lack of security and the results thereof are talked about much more quietly. Instead service providers and technology delivery partners prefer to speak of uptime, and resilience. It is hardly surprising that what we don’t hear mentioned is who suffers from fraud. Big consumer data breaches hit the headlines frequently though only vast corporations like Target, TalkTalk and Sony really hit the headlines of the business community. Target was the result of a third party supplier breach but the snowball effect affects the entire business community.
Fraud is perpetrated every day. We fear being the victim but the reality is that often we are the problem as much as we are the solution. The IT and Telecommunications industry’s challenge is to effectively address the “elephant in the room”. Talking about fraud with clients is interesting because service providers don’t want to sell on ‘fear’. Yet, at the same time, when they provide only one aspect of client infrastructure (e.g. telecoms), they may have no direct control over the infrastructure or the end user’s business or employees. When ‘fraud’ is perpetrated the initial and historical reaction is ‘fire fighting’ by identifying the cause and implementing a solution. Finally, they determine who gets the blame. One thing is certain, regardless of ‘fault’, the provider’s brand is damaged simply by association.
This first post is an examination of:
- The Telecoms and IT security in the UK
- Technical best practice
The second post addresses:
- The human wild card
- We need a new way of thinking
Perfect solutions may not be available, but by removing the most painful and immediate result of a telecoms security breach – the financial cost – companies can change the way they approach security. Removing the risk of an expensive pay-out – which a service provider does not want to request, nor a client receive – massively changes the dynamic of the whole security equation.
By removing the risk, core stakeholders can then (in theory at least) work together in a cooperative, and constructive ways to firstly, ensure that a process of best practice is implemented, but also ensure that the cause of most hacks – human error – means that scapegoating and blame can be turned into a justification and positive reinforcement exercise that strengthens the client’s focus on increasing their information and network security across the board. Happy clients mean happy service providers and protection for the industry’s reputation.
Telecoms and IT security in the UK – where are we today?
In 2015, Telecoms and IT security are one and the same. A Legacy or IP PBX, or IP handsets are simply network devices that can provide huge business benefit and are crucial to most business operations. They are, however, devices that must be managed carefully along with every other network device so that they are not open to misuse. Similarly to the Local Network, infrastructure services like ISDN and SIP Trunks must also be managed, and some legacy services such as ISDN have more inherent risks associated. PBX security does not happen ‘out of the box’, it requires careful planning and control of both the network and connectivity.
Worldwide spending on Information Security showed an increase of 7.9 percent on 2013 and is predicted reach $71.1 billion in 2014 and to grow a further 8.2 percent in 2015, with roughly 10% of security capabilities delivered through cloud services1. Malware and processing power are available on an industrial scale at relatively low cost and businesses must prepare themselves to prevent becoming targets.
An enormous telephony bill at the end of the month, for some, could be the only indication that they are the victim of Telecommunications fraud. A frightening situation for anyone – be it the business owner or the IT Manager responsible for making sure that such a situation doesn’t happen. What is the initial reaction? Apportion blame? Deny liability for the costs? Fire a supplier or an employee? Contact the police or seek remedy in court? Two things are certain, a business will not be happy to pay such costs; and the resulting fallout can destroy even the longest standing business relationships.
The first question is what we can define fraud as? Is it simply exploitation of third party resources for financial gain? Or does it also extend to company employees costing their employer more, by extending their use of services provided by the company for personal benefit? We work on the basis of the full definition and focus on any expenditure that would not have been authorised by a company (in relation to their Telecommunication systems) is fraud.
Experience to date shows that the costs of fraud often never see the light of day. The reporting rate to the police the Action Fraud Bureau is just the tip of the iceberg. The Telecoms industry has been forced into a position where liability is the responsibility of the end clients simply to protect their own businesses, which in turn stimulated the development of the entire Info Security industry.
European Commissioner Neelie Kroes, Vice President for the Digital Agenda, was typically direct in her views of the Telecommunications industry: ‘Sometimes I think the telecoms sector is its own worst enemy.’ She went on to ask whether we will be leading the industry or whether we will be dragged ‘kicking and screaming’2. This may seem negative, but the Telecommunications industry has been around for over a hundred years, and like many mature industries, change can come very slowly. While consumer telecoms, driven by the likes of Apple and Samsung, has commoditised the industry and radically adjusted consumer perception, the more traditional business to business market moves much more slowly.
The business and technical challenges
The fact is that we, as providers of telecommunications services, are providers of business critical services; the security of which we don’t necessarily have control over. This seems counter intuitive, doesn’t it? However, the challenge does not end there; types of exposure to fraudulent activity can vary significantly depending on a number of factors, not the least of which is the actual size of organisations.
For example, a company with 5 employees may have no IT expertise in house; they could rely on outsourced network support (or no network support at all) and leave themselves exposed on a variety of levels. A FTSE100 company on the other hand, may have an IT department consisting of dozens (or even hundreds) of staff, with a multimillion pound budget, but the sheer volume of devices that access their network and potential complexity of the network alone doesn’t offer them certain protection. Consider the recent cases of Home Depot and Target in the US, for example, who were penetrated at the point of sale at a cost to their own brand and their bottom line.
So what are the key considerations when it comes to telecoms security?
An onsite PBX is inherently vulnerable.
Physicality – As we know, unless equipment is in a secure environment with biometric and prescribed access control procedures, the PBX can be accessed and call routing tables amended. Note that organisations such as the NICC refer to a plethora of documentation in respect to best practice for such installations; however, how many companies are in a position to adopt such best practice?
Unauthorised access can be gained by anyone, from a systems administrator to a cleaner.
Remotely – many PBX’s are connected to the internet to enable remote access from their providers and to interface with cloud servers such as Jabber for IM and contact centre technologies, for example.
The first challenge is securing the local network, such as blocking port 5060; however, who controls the network? Is it the IT support company (in-house or contracted) or the communications provider? More often than not it is both – two brains potentially acting separately. This creates grey areas of responsibility as demonstrated by a recent High Court case where £35K of fraud was held against the communications provider.
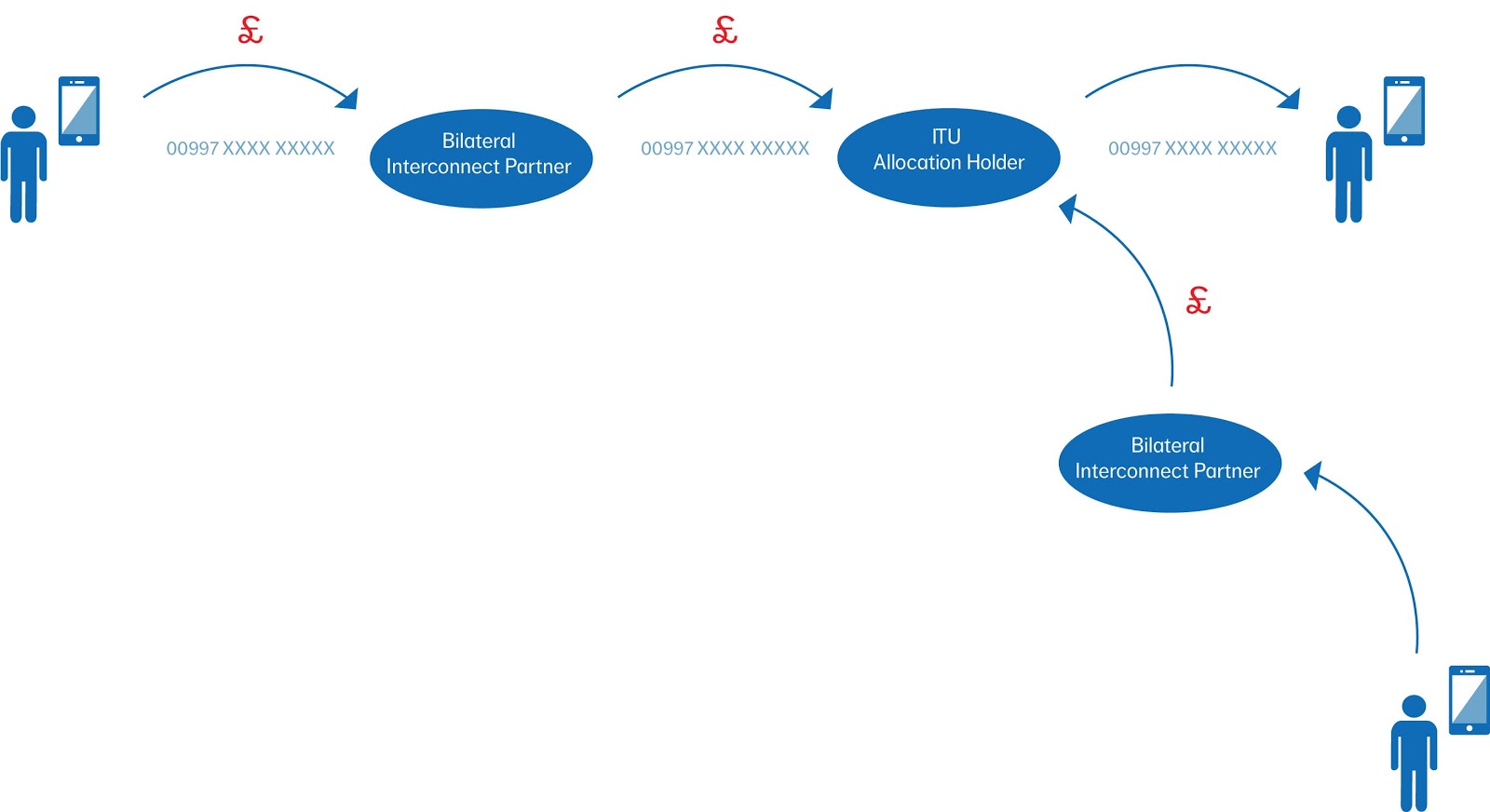
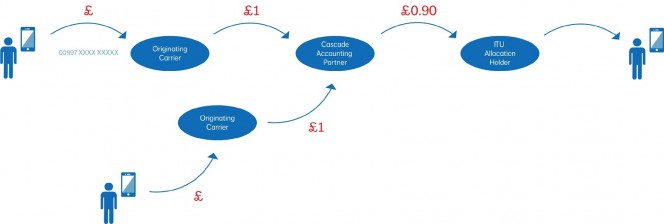
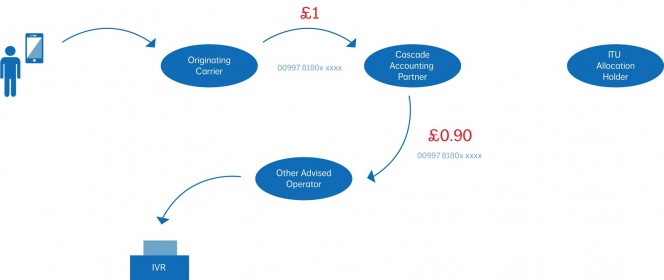
There are two principal methods by which fraud is perpetrated:
- Hacks over the internet
- Dial-through fraud – Hacks via voicemail pin
Both of these methods aim to divert traffic to premium rate numbers (usually international) whereby the fraudsters are rewarded with the profit generated from such numbers.
What about at a national and global level?
Typical Methods of Prevention
The Telecoms supply chain can be very complex. A carrier provides minutes to a sub-carrier and in turn to a reseller and in turn to, say, a SIP trunk provider and then again to the end client, or indeed another reseller. There are many combinations and permutations in the supply network.
What about at a Carrier Level?
Responsible carriers will offer protection using two principal methods:
- Referring to a fraudulent number repository – and blocking calls to such destinations
- Algorithmic – detecting unusual traffic patterns and blocking calls accordingly.
At Sub-Carrier Level
- Credit Limits – Imposing credit limits on resellers globally
The only real way to protect against fraud is the intelligent and real time monitoring of call traffic via Call Detail Records, or the logging of minutes. The challenge the reseller community has is that they are reliant on carrier provided monthly CRDs which only deliver the information after an incident has taken place, over a period of time. A very large cost can be accumulated in the space of an hour, let alone a month.
There is a major consideration too for the reseller community: They will have a company credit / supply limit with their SIP Trunk carrier globally. If that reseller hits their credit limit an automatic block on their services is implemented (automatically); that could potentially mean a block on all of their clients trunk services – a total service outage in effect. It is absolutely crucial the telecoms channel be able to manage their client base at a granular level and in real time.
This is telecom fraud week on trefor.net, edited by Manuel Basilavecchia of Netaxis. Read our other fraud posts this week:
Colin Duffy on “is encryption the answer to data loss”
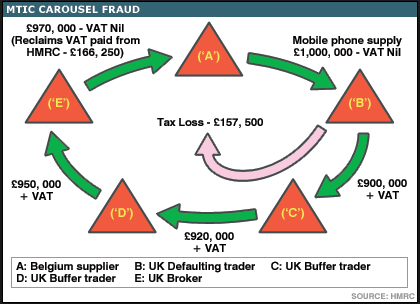
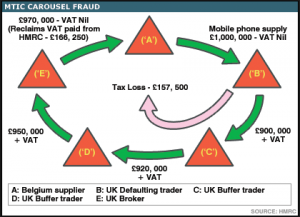
Manuel Basilaveccia on Missing Trader VAT Fraud
Dave Dadds – “telecom fraud is industry’s problem not the customer’s“
Manuel Basilavecchia on “A mobile operator fraud case study”
This post is an adaptation of an article first published by Jonathan Rodwell last year in the Journal of the Institute of Telecoms Professionals but is only available to members behind a firewall.
In his second post, to be published tomorrow at 1pm Jonathan conclude by looking at
- The human wild card and
- We need a new way of thinking
1 Gartner Press Release, Sydney, Australia, August 22nd 2014
2 Adapt or die: What I would do if I ran a telecom company, FT ETNO Summit 2014, Brussels, October 1st 2014