Big fuss doing the rounds over the Heartbleed bug. Google it. Every man and his dog1 is saying it is really bad and offering advice which basically says change your passwords oh and btw it might not make sense to change it yet because your specific service might not have patched their SSL.
Now this is the problem. I have 75 sets of credentials for accessing online services. Each one has a complex and unique password. It’s going to take hours to change them all.
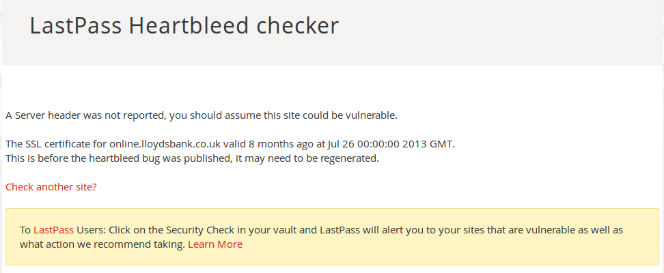
A few are more important than others, Google and banking for example. I checked Lloyds Bank. There are no notifications on their website. No advice. No words of comfort saying “don’t worry Tref you are ok son”. Now I can’t believe that a bank like Lloyds with presumably a huge security team hasn’t got it covered.
I checked them using LastPass and got the message “A Server header was not reported, you should assume this site could be vulnerable.” Now this may be because the site is vulnerable or it may be that Lloyds has its website nailed down so that services such as LastPass can’t ping it for information. Not being an expert in this field I don’t know.
Maybe I don’t need to worry about it anyway. Lloyds uses 2 factor authentication. Is that affected? Hmm. No idea.
I read about tech so picked up the Heartbleed story. My dad doesn’t read this stuff. He is 80. He reads the sports pages, the political news and, oh I don’t know, headlines from 1956. Anything really but not news about Heartbleed. Yeeeeoooooooowwwwnggg – right over his head. He probably doesn’t even know most passwords he has created. Probably a majority of the population will be in the same boat.
A lot of people out there will be oblivious to Heartbleed, oblivious to whether their services are affected and oblivious as to whether they need to do anything about it. What’s to do?
I’d envisage each of the 75 services I have an username and password with will be wanting to send me an email advising me of a course of action. Not received one yet…
Other security related posts:
Who sells your contact information?
1 Rover2
2 Could be Bonzo

4 replies on “Heartbleed – a pain in the proverbial”
I’m doing nothing. It’s a vulnerability, I haven’t seen evidence of it being exploited. Passing new credentials through a potentially compromised service seems pointless.
Grabbing 64k chunks of RAM content sounds like a fairly hard to exploit vulnerability, doesn’t it ?
We are on the same page Phil. It’s a combination of the size of the task versus whether the service has been patched.
The media loves a great scare story though.
Yes, for once the headline – the vulnerability – is actually true. After that it’s all downhill.
The problem is that it is very easy to exploit, you don’t have to do anything complicated to take advantage of this bug. Metasploit has a script that will test this vulnerability and it is just straight forward request/response code, no bashing through security barriers, no convoluted steps of gathering data to patch together, you just send a heartbeat request and *lie* in one of the fields. Due to the way the memory allocation works a lot of the boring code like application start up etc won’t be returned, you are highly likely to get a recently used block of memory, which in a high volume service like a bank or yahoo is incredibly likely to contain session data, usernames, passwords. This *is* a vulnerability that is worth worrying about, however at this point doing nothing is the correct approach. Ideally any service you use that has been vulnerable will contact you *after* they have patched the bug *and* revoked their old SSL certificates. If they don’t revoke their old SSL certificates and have been victims then their users are in great danger from Man In The Middle attacks. Not seeing evidence of this being exploited should not be too comforting, due to the banality of the heartbeat request many companies won’t have set up their systems to properly detect this kind of intrusion, it was never considered an avenue for attack. 64KB might not even sound like a lot of data but imagine a thousand computers on a bot net exploiting this thousands of times a second? Next to no effort for the blackhats out there.