Online rights framework will help safeguard privacy
The internet is increasingly key to our daily lives and a crucial part of public policy making with ramifications across all areas. However, too often what we get from politicians is poorly thought through kneejerkery. I’ve seen this myself, on far too many occasions.
Just to pick up a few examples, when we were re-writing the Defamation Bill, there was a proposal being pushed that ISPs should be required to filter out any defamatory content on their network – quite a tall order.
David Cameron has been particularly bad – you may remember his suggestion at the time of the riots that he should be able to turn off social media to avoid panic. It took a lot of work to stop that and make it something that was ‘not even considered’. More recently, he’s been insisting that we should ban any messaging system that cannot be decrypted by GCHQ, completely failing to understand the essential link between encryption and cyber-security.
But this problem strikes the opposition too. There have been some really alarming comments about filtering out legal material online that completely miss the point of what is technically possible or desirable. And of course there are people in each party who do actually get it, although not all of us get to have the necessary influence over our front benches to achieve sensible outcomes.
My party has taken these issues seriously, and there are several things we hope to achieve in this area. One of these is stable sensible regulation – something that almost shouldn’t need to be said. Brilliant new ideas can easily be killed off if regulation is tweaked unexpectedly and long term investment will drop off if there is a risk of irrational rule changes. We as politicians should set a framework of principles, which should then be relatively stable. We should call on technical experts for help and have discussions with the community and businesses. We can then setting the detailed online rights rules in a rational way. That has to be the best way forward.
I’ve been particularly working to develop a Digital Bill of Rights, setting a basic framework for what people should expect online when it comes to issues like privacy, net neutrality and more. This has become especially important since the Snowden revelations. All of us want security, and all of us want privacy. How do we try to achieve both of those goals? When should the police or security services be allowed to collect information on us, and for what purposes?
Typically, these issues have been dealt with largely secretively and reluctantly, and with a focus on specific data types. For example, strong controls were introduced on DNA data in the Protection of Freedoms Act, but the Police just sidestepped them when storing biometric information, without even attempting to learn the principles from DNA data.
So those are my two key points – stable and sensible regulation, and a clear principle framework for our online rights. If I’m re-elected I’ll fight for those but it would be great to have more colleagues to help with that.
If you want to help me achieve this vision, please consider helping me out – http://www.backjulian.co.uk has the details.
Julian Huppert is Liberal Democrat MP for Cambridge. He has a scientific background and is one of a very small minority of our MPs who can grasp issues relating to internet technology.
Although one or two more might creep in that pretty much concludes the week’s posts on advice to the next government. Other political week posts on trefor.net are linked to below:
James Firth on why government should stop looking to big corporates for tech innovation
Gus Hosein on Data Protection Reform and Surveillance
The Julian Huppert crowd funding campaign here
Paul Bernal suggests government should hire advisers who know what they are doing
Domhnall Dods on Electronic Communications Code reform
James Blessing Says “No matter who you vote for…”
Peter Farmer on Ofcom really isn’t an all powerful deity
Dr Monica Horten on Why the Magna Carta applies to technology policy
See all our regulatory posts here.

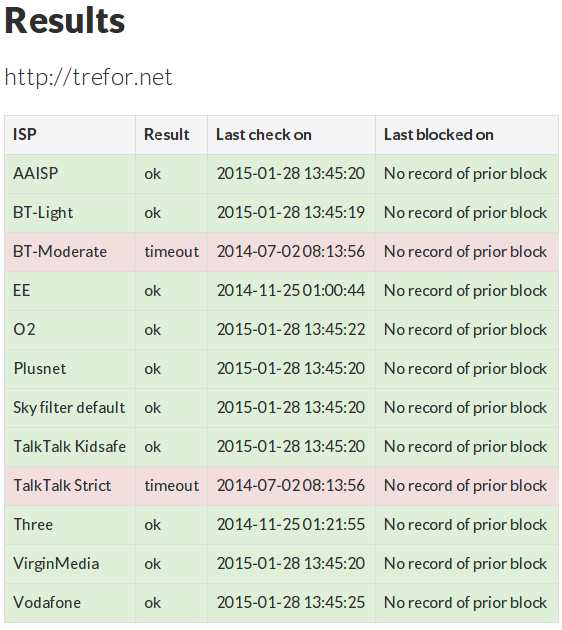


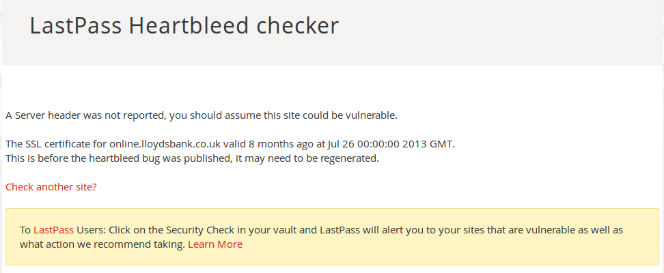




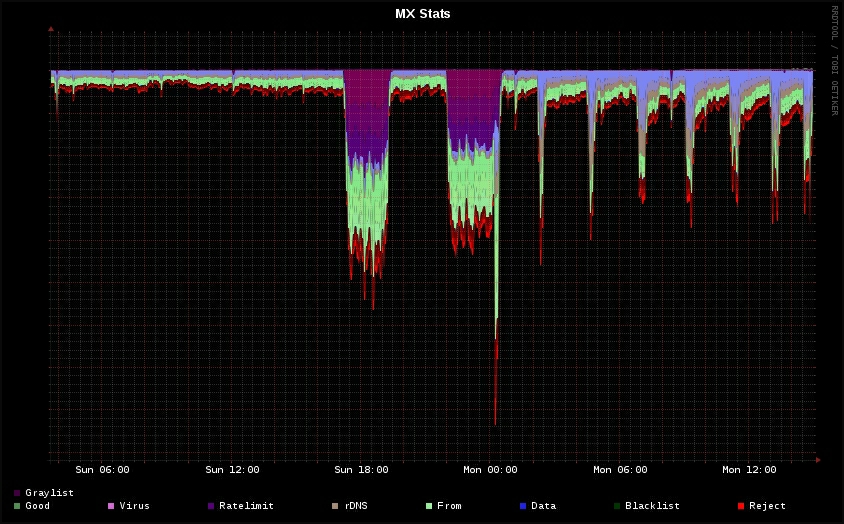 Microsoft will have a huge team of people managing their email platform. That spam was identified is also a testament to the Google anti spam capability which is widely considered to be the best in the game.
Microsoft will have a huge team of people managing their email platform. That spam was identified is also a testament to the Google anti spam capability which is widely considered to be the best in the game.