SME cybersecurity – should they care?
Small retailers and businesses aren’t doing enough on cybersecurity. This, at least, is what emerges from a survey published recently from domain provider 123 Reg, who canvassed 13,000 online retailers and discovered that 10% of them aren’t taking any steps whatsoever to protect their customers’ personal data.
This is a worrying figure, and while 10% isn’t perhaps a massive percentage on its own, the survey also found that 50% of e-commerce owners admit to not being prepared for an attack and to not having a recovery plan in the event of a breach.
While such findings are already disconcerting enough in simple terms of cyber and data security, they’re also troubling for another reason, which is that they reveal how smaller online retailers are jeopardising their businesses and their trustworthiness by neglecting the security of their websites and platforms.
This isn’t something suggested only by 123 Reg’s recent survey, but also by other research. For example, in June 2016, Barclaycard conducted their own survey on SME cybersecurity, learning that only 20% of small and medium enterprises held up online security as a top business priority. This was despite the fact that 48% had knowingly been the victim of a cyberattack and the fact that 54% were concerned about hacking.
And this stands in marked contrast to larger enterprises. Larger businesses take cybersecurity more seriously and invest more in it, with the latest Thales Data Threat Report revealing that 73% of large international corporations will be increasing their security spending this year. Similarly, the report also shows that 88% are highly concerned about data security, while a similar Zurich Insurance survey of SMEs from last year found that only 8% rank cybercrime as the top risk to their business.
Of course, larger companies are targeted in more high profile ways than their smaller counterparts, yet what should be unsettling for SMEs is that attacks against them are on the increase. In 2016, smaller businesses were hit by some 230,000 attacks, while the percentage of breaches targeting SMEs grew from 18% in 2011 to 43% in 2015.
One way of interpreting such growth is that, as cybercrime grows and becomes almost ‘professionalised’, cybercriminals are increasingly realising that smaller retailers are a soft target. And as the surveys mentioned above indicate, this is because SMEs aren’t devoting enough attention to the security of their websites, servers, networks and platforms.
As a result of this inattention, 74% of SMEs suffered an information security breach in 2015, according to Government figures. And this proportion is likely to grow, especially in light of how an August 2016 survey from Close Brothers revealed that 63% of SMEs have actually decided not to invest in improved online security in light of the EU’s General Data Protection Regulation.
Somewhat luckily, SMEs lack the kind of visibility that would result in breaches being widely reported in the media. However, if attacks against them do indeed continue increasing, and if the public become increasingly aware of these attacks, then trust in smaller online businesses and retailers will be damaged.
And as the notorious TalkTalk hack from October 2015 plainly revealed, a violation of customer data wouldn’t result only in a loss of trust, but also in a loss of customers. And for smaller retailers and businesses eager to hold onto as many of their customers as possible, such losses would be very damaging.
It would result in small and independent retailers losing even more custom to giant online outlets such as Amazon and eBay, in the process strengthening even further the stranglehold such larger companies have on digital spending and shopping. At the moment, a whopping 55% of all online product searches are made on Amazon (at least in the US), and this share will only increase if SMEs continue being too inactive on cybersecurity.
This is why, even with smaller budgets, SMEs must take greater action to strengthen their data and cyber security. More of them need to adopt such measures as multifactor authentication for important company accounts, drawing up contingency plans for cyberattacks, conducting regular tests and assessments of the strength of their cybersecurity, and tightening physical and online access to sources of sensitive information.
By taking such steps, and perhaps by going so far as to employ dedicated information security officers where possible, SMEs will be in a much better position to guard themselves against the rising tide of cybercrime.
Yet more generally, they’ll be in a much better position to guard their businesses, their reputations, and their relationships with their customers. And given that they make up 99% [PDF] of all UK businesses, they’ll also be better placed to protect the British economy at a time when it needs more than ever to grow.
This is a guest post by Simon Chandler, News Editor of Choose, a consumer price comparison and information site covering broadband and personal finance services. Simon wrote the post a few weeks ago and I’ve been a delinquent in sticking it up. I don’t typically take guest posts from sites who are doing it for their own SEO benefit but in fairness to Choose they supply good quality copy and I wish them well with it.










 As regular readers will know I don’t use Microsoft software anymore. I’ve suffered from so many
As regular readers will know I don’t use Microsoft software anymore. I’ve suffered from so many  Last week the license ran out. McAfee bless em wanted £59.99 for me to renew. I looked online and saw a number of deals including a lowball £25.50 but decided to nip into PC World so see what they had.
Last week the license ran out. McAfee bless em wanted £59.99 for me to renew. I looked online and saw a number of deals including a lowball £25.50 but decided to nip into PC World so see what they had.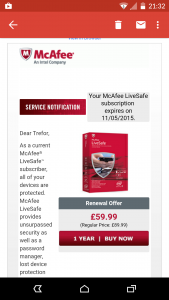 The salesman/advisor simply suggested Norton at £40 (£39.99). No problemo.
The salesman/advisor simply suggested Norton at £40 (£39.99). No problemo.

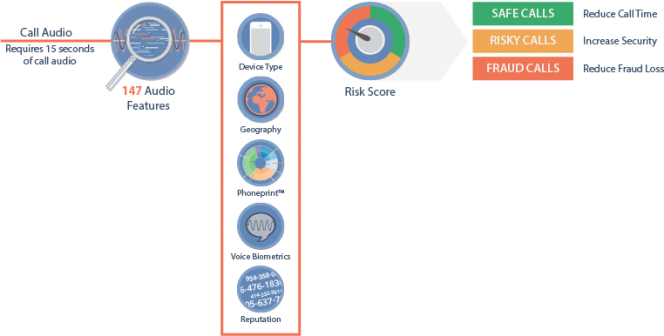
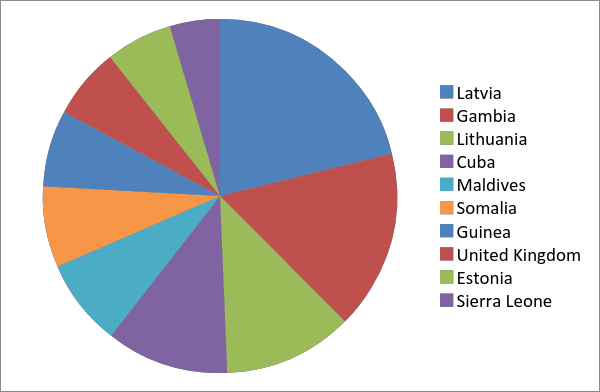

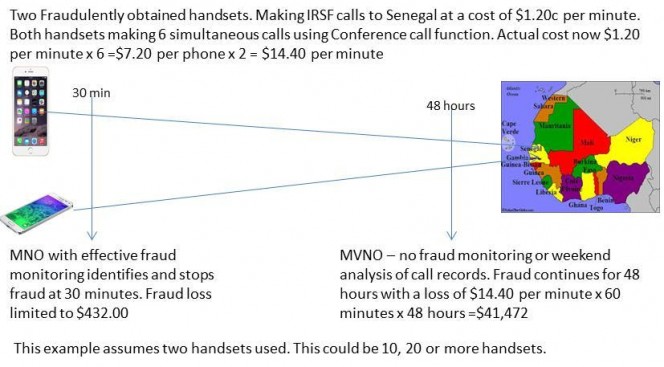



 IP Phone Security ensures IP Telephony is not compromising the business
IP Phone Security ensures IP Telephony is not compromising the business