VoIP fraud continues to rear its head this week with a post on ISRF mechanics.
Continuing with his week as guest editor covering VoIP fraud issues David Cargill has invited industry expert Martin John from AQL to discuss IRSF mechanics – how it actually works:
As we all know International Shared Revenue Fraud (ISRF) plays a large part in the overall fraud that we see in the industry, even though services are marketed legitimately they are widely used for fraudulent purposes and the artificial inflation of traffic, whilst some of the traffic will terminate in the target country a high percentage will never reach the expected destination (commonly referred to as short transit or short stopping)
Whilst the ITU governs the allocations of Country Codes once the code is allocated the usage and numbering plan is controlled by the responsible authority in the recipient country, the ITU publishes updates on the reported use of each numbering block for each allocated Country Code (http://www.itu.int/oth/T0202.aspx?parent=T0202) however this is based on information submitted by the responsible authority and is not always an up to date source of information.
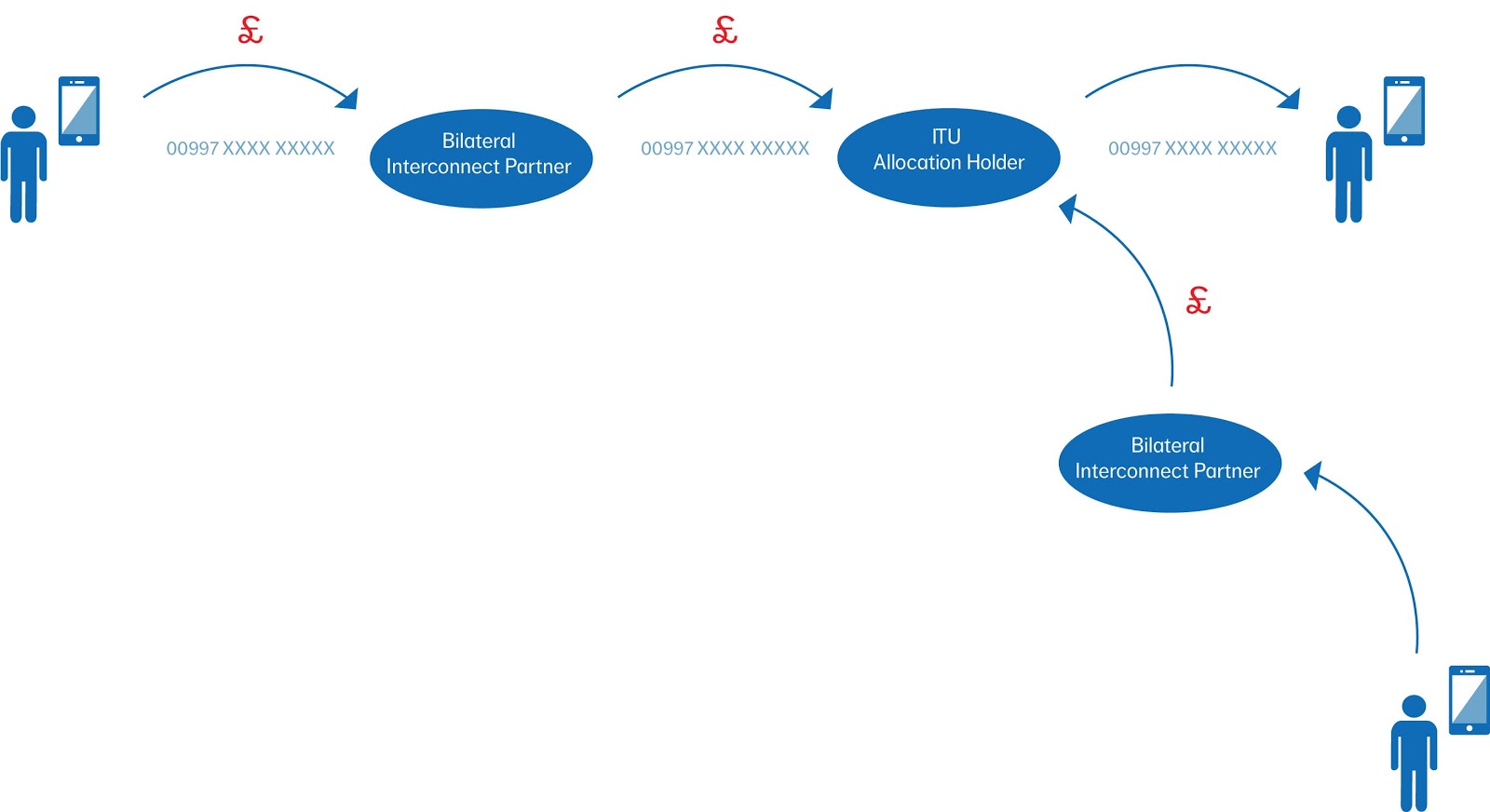
Historically Telecoms Operators interconnected directly via TDM on a bilateral basis, a settlement rate would be negotiated with a key objective being the balance of traffic to reduce any financial settlement between the parties, using this method the majority of ISRF traffic actually terminated in the country that holds the number allocation.
Smaller countries or those with financial constraints could not justify or afford this method and opted for a cascade accounting method, cascade accounting meant that the smaller operator would make an agreement with one or two larger international operators whereby the larger operators became an aggregation point for the allocated country code and in return kept a percentage of the revenue.
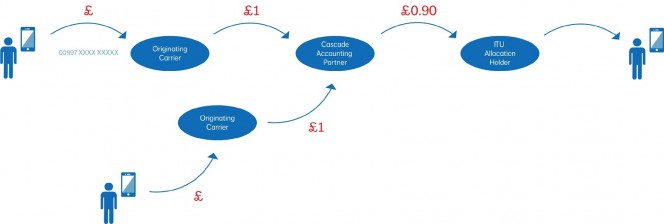
With cascade accounting traffic to designated number ranges could potentially be short transited, the authority responsible for the allocation and administration of the number ranges may have requested that the cascade accounting partner terminate certain prefixes to alternate carriers/partners for other services, these opportunities were very financially rewarding due to the expensive part of the network (the international circuits) not being utilised.
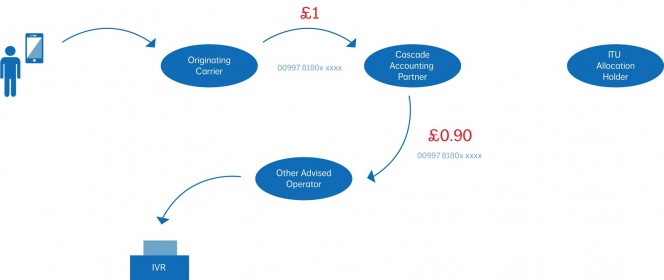
As the market developed and with the establishment of VoIP clearing houses/exchanges and traffic aggregators cascade accounting has become less popular, operators favour being able to interconnect to lots of different operators in one place, increase their profitability as they no longer have to give a percentage to the cascade accounting partner and lower their cost base as they would no longer need to purchase other international routes via their previous cascade accounting partner, however this simply made ISRF easier, the telecoms market is more cost driven today than it has ever been operators strive to maintain lcr with the minimum of man power and international destinations that are outside of their main business area are commonly terminated through large traffic aggregators or clearing houses, interconnection between the aggregators and clearing houses is a common practice it is in their business interest for a call attempt to complete and convert to revenue and therefore as the financial barriers to connect to clearing houses are small the interconnection by parties that want to abuse the situation is relatively easy.
Take for example the following scenario:-
The island of High Termination Rate is assigned the country code of +997 from the ITU the and files a numbering plan. The island of High Termination Rate Telecommunication Regulatory Authority (HTRRA), announces the following:
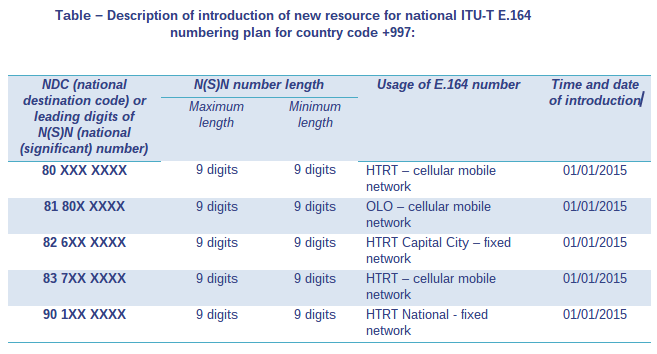
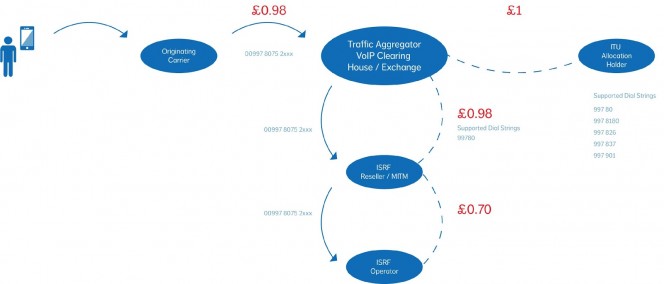
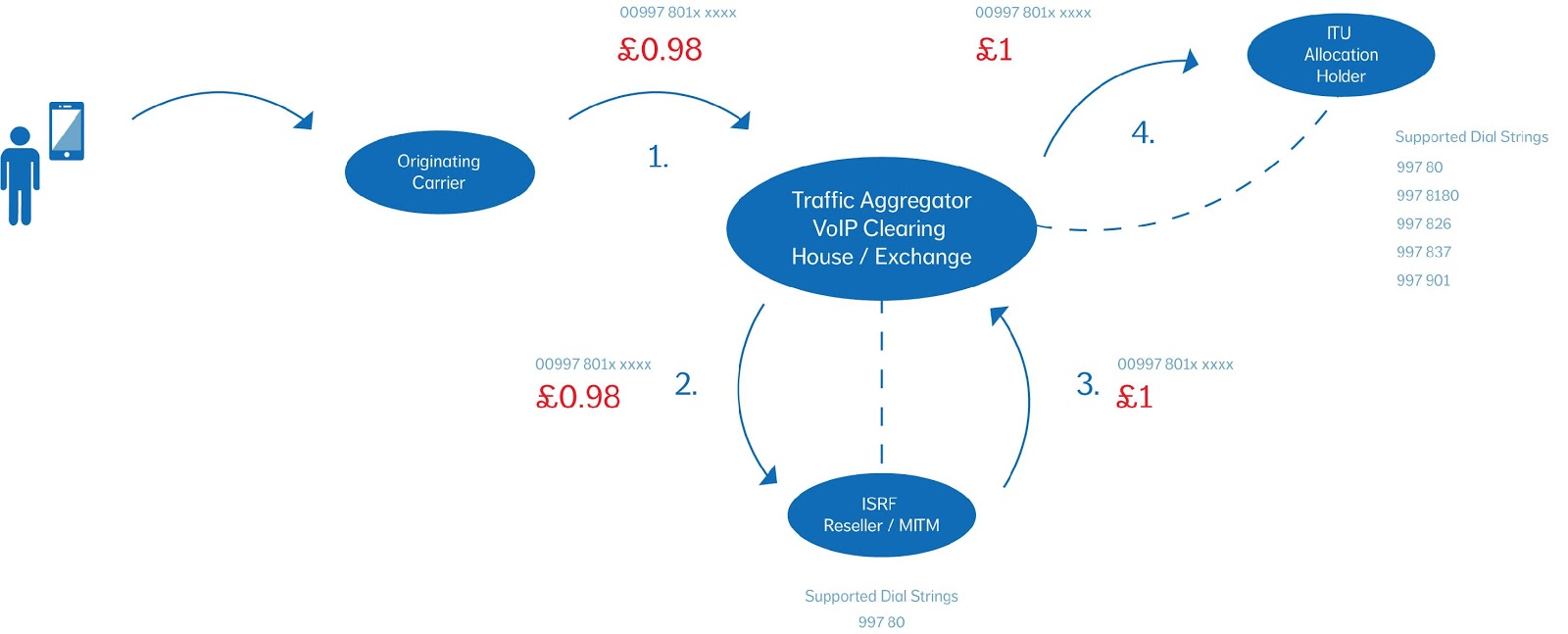
The national operator of the island of HighTerminationRate HTRT is a respectable and ethical company that interconnects to a large traffic aggregator and a clearing house to not only gain access to a full international A-Z for terminating traffic but also to ease interconnection with other international carriers so that the residents of The island of HighTerminationRate are globally reachable, the per minute rate is advertised as £1.00 ppm
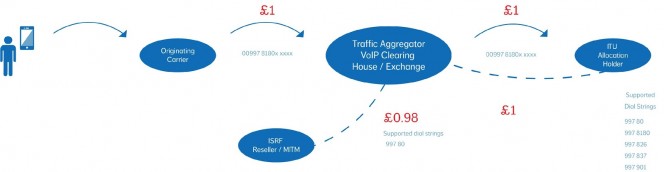
To this point everything is legitimate however there is nothing stopping the aforementioned opportunistic man in the middle/ISRF reseller from also interconnecting to an aggregator and clearing house and advertising a rate of £0.98 ppm supporting either the full list of breakouts or “specialising” in certain areas such as HTR Mobile +99780
In the background the ISRF reseller has been busy harvesting numbers and happily upsetting the observed statistics (reduced ASR’s etc) whilst tying up network capacity to obtain a better understanding of the utilisation of the ITU allocation. Once this understanding has been obtained numbers can be tested and resold to customers.
Some may wish to offer chat services or other services of the like whilst avoiding any national regulation and of course this then opens the door to parties that wish to generate fraudulent traffic. To expand further after number harvesting it is discovered that anything that starts +99780752 can NOT be completed via the legitimate route offered by HTRT. It is a range that falls within the allocation but perhaps due to demand has not been opened yet.
Any traffic generated to this range will fail on the HTRT route if in fact it even attempts the HTRT route first due to the ISRF route being marketed at a lower rate. Once that call has failed the aggregator/clearing house would normally route advance the call to the next available route where ISRF are happy to complete it. Legitimate traffic that the ISRF route receives is simply terminated back to another carrier. Whilst this incurs a loss with restrictive routing and capacity the impact is minimal and aesthetically legitimises the service offering provided by the ISRF route.
Martin John is the General Manager of aql wholesale. aql, established in 1998, is a wholesale integrated Telecommunications Operator, Regulated by Ofcom. Providing services to many of the FTSE 100 and is one of the UK’s largest IP Telephony fixed line operators. It is recognised as a significant market force in fixed and mobile services by the UK Regulator.
Check out our other VoIP fraud posts here. Below are links to other fraud related posts this week:
PABX fraud by Manuel Basilavecchia here
IRSF Fraud by Colin Yates here
CLI Spoofing detection by Matt Anthony here