Startup lessons learned
The CTO of a failed British company discusses startup lessons learned (not my business btw TD)
1. Your earliest staff are partners – treat them as such
Lack of funding security is the inescapable reality of any early-stage tech start up; you live each day thinking about where the next batch of funding comes from. As such any early staff you have, like it or not, are living the same rollercoaster as you.
Moreover you can’t afford resilience and redundancy of knowledge. Your lead developer can take the business down any time simply by walking out. You need to square the power/reward/responsibility equation from day 1. The longer you leave this to fester the harder it will be to sort out.
2. Good ideas are ten-a-penny, good businesses are something else entirely
When starting a business to bring a new product to market the hardest problem you will encounter is building a scalable business around your product.
Even today many people seem to overvalue their product idea. I say even today because if there’s one thing the internet has taught us is that truly original thinking is as rare as a Googlewhack.
If you still think the initial idea is worth more than anything else to the business (which, in a few cases, it might be) please bear two things in mind: your idea is probably not original; and, even if it was, originality itself is no guarantee of success in business.
This makes a mockery of the idea of “protectable IPR” so many investors get hung up on. The notion that someone else will steal your idea and make it work before you get your product to market is only applicable to a minority of businesses where the idea is discrete and so overwhelmingly compelling and clearly valuable [typically in an existing market].
In most cases there will be a significant risk associated with bringing the idea to market. Consequently anyone with the resources to steal your idea would probably rather sit back and wait to see how you fair building and scaling your business before jumping in to steal your market share. See point 3.
3. Absence of competitors sucks
Building a market is far harder than building market share. In fact it’s harder than building the product itself.
When you launch a new product in an existing market there’s stacks of people out there who already know there’s a solution to their problem. Your biggest challenge is getting onto the buyer’s radar; and then distinguishing yourself from your competitors. And there’s a solution to both of these: money (on branding and marketing).
For a brand new product your challenge is to find people who don’t know there’s a solution to their problem. People who are not already out there actively looking for a solution. In fact you’ll probably spend a significant amount of time convincing your prospective customers that they have a problem in the first place.
4. FFS listen when somebody tells you, “fail hard, fail fast”
This should be a no-brainer but my business partners and I were told this in the strongest terms on day one but still succumbed to the fear of loss rather than making rational decisions based on a sound plan.
Failing slowly over several years costs far more than ramping up quickly and bailing early, even without taking into account the ongoing soft spending and personal toll on all involved.
Loss aversion is the theory that says we hate losing more than we like winning. This can have two major consequences on a start-up:
- We hold back funding for fear of losing it. This pretty much rules out failing hard because no-one’s willing to put all their chips down on day one.
- Even when we realise the company is probably not going to succeed we don’t pull the plug for fear of losing what we’ve already invested. We look to keep the dream alive for as long as possible.
The answer is, unfortunately, simple: be prepared to go all-in on day one and pull the plug on Day 6 if it transpires the New World you built isn’t worth living in.
The Fail Fast approach has the added benefit of getting your product to market relatively soon after the initial development. Selling a product designed 3 months ago is easier than selling something built 3 years ago in the fast-moving tech world.
It’s also easier explaining to potential investors why you haven’t got sales in the first year, than it is explaining this in year 3.
5. New ventures are built on personal energy and no, you can’t delegate your enthusiasm
Background/silent partners can be great; so long as they’re (a) aware of what they’re getting themselves in to and (b) sufficiently tolerant to the risks and day-to-day rollercoaster any new venture inescapably becomes.
However, in my experience at least, few background partners remain silent. If you, as a major investor, also want to act like the boss and steer the day-to-day running of the company, you need to sit there as the CEO and run the company.
Building a new company is bloody hard work and probably needs to be your sole focus for the foreseeable future. If this isn’t for you then consider either the silent partner option or whether you really want to get involved at all.
If you’re too busy with other ventures to run your new company what you absolutely cannot do is bring in “your man” (or your lady) to run it for you. It’s unlikely whoever you choose to run the company on your behalf will convey your personal enthusiasm, and it’s highly likely the rest of your partners will resent having to deal with you through your chosen intermediary/enforcer/patsy.
6. Too many cooks…
For every founder of a new venture to qualify for the UK’s Enterprise Investment Scheme (EIS) a company needs at least 4 founders, since no single shareholder can exceed a 30.0% holding.
Since EIS (and SEIS) relief is so attractive to investors (they essentially get a third of their investment back in tax relief, plus additional relief on capital gains on exit) many UK investors insist on EIS status.
An unintended consequence of becoming attractive to investors, as well as getting the most from your own investment, is you need to invite 4 cooks into the kitchen before you’ve even fully worked out the menu.
Queue the inevitable in-fighting and grandstanding as everyone strives to defend the value they each bring to the company.
Also, with share allocation spread relatively thinly from day 1, any future dilution, however necessary, starts to look extremely unattractive.
So… Start small and forget about investment relief, for now. That’s a matter for your future investors and can be solved later (despite what your accountant tells you – there are always options, like creating a new parent company).
As founder (or founders) your only objective is to build and demonstrate a viable business.
7. The UK is not California… And it never will be.
UK investors suck. Or at least I thought that for quite a long while.
The key message here is that as a pre-revenue tech start-up you’re unlikely to be showered with cash based solely on an idea (see also point 2) because the majority of investors here look very hard at the extent to which your idea is likely to scale before investing significantly into risky ventures.
And because you need some revenue and a demonstrable uptake curve to prove your scalability you’re highly unlikely to get significant investment until you have multiple sales.
Consequently, pre-revenue companies need to rely on Business Angels for their early funding, because many Angels will make a decision based on gut feeling, however this somewhat limits your ability to scale early (see point 4).
But I have reconciled myself with this approach as it reduces the waste, folly and premature champagne exuberance of some Silicon Valley ventures (yeah we have a website launch, let’s PARTY..!). That, ultimately, means more money in the pot – and on better terms – for those who make the cut.
8. Don’t think about the end before you’ve started and definitely don’t expect anyone but you to share your own aspiration and self belief
Ok this goes against the accepted wisdom of setting your sights on a target and sticking to it, and also the advice of many investors to start with an exit plan.
But what I’m talking about here is starting off with the attitude that you’ve just founded a £10m company.
It’s all very well having ambition and drive, and a target for your new venture to be worth £10m in 3 years’ time. But confuse aspiration with reality at your peril as you will, inevitably, overvalue what you currently have and undermine the amount of work left to achieve.
When you offer your developer 10% on day 1 you’re not writing a cheque for £1m. You’re giving him or her a reason to ride with you on your journey and stick with you over all the bumps along the way (see point 1). Besides this will be diluted anyway.
Overvaluing what you have can pollute so many decisions, from turning down much-needed cash because you feel your company is being undervalued, to setting up appropriate share-based remuneration schemes because you can’t imagine why the digital equivalent of a plumber should get £50k of “your money” (reality: £500 – for a year’s work).
Above all else it can give you a clouded view of what still needs to be achieved to reach your target valuation.
Your company is worth what an external investor is willing to pay, it’s as simple as that. Everything else is your aspiration – which is all very well but don’t expect anyone else to share your belief in yourself; go out and prove it!
 When you think about it when do you ever engage with friends on YouTube? Never? It isn’t the same answer on Facebook. Videos posted to Facebook are therefore far more likely to spread virally than YouTube. Certainly in our experience.
When you think about it when do you ever engage with friends on YouTube? Never? It isn’t the same answer on Facebook. Videos posted to Facebook are therefore far more likely to spread virally than YouTube. Certainly in our experience.

 If I lived in Brum, Coventry, Derby, Chesterfield, Leicester, Milton Keynes, Nottingham, Oxford, Stoke on Trent or Wolverhampton I’d be ok. Maybe.
If I lived in Brum, Coventry, Derby, Chesterfield, Leicester, Milton Keynes, Nottingham, Oxford, Stoke on Trent or Wolverhampton I’d be ok. Maybe.


 Our guest speaker on this occasion is regular trefor.net contributor Lesley Hansen.
Our guest speaker on this occasion is regular trefor.net contributor Lesley Hansen.




 Lyndsey Burton comments on Digital Single Market
Lyndsey Burton comments on Digital Single Market

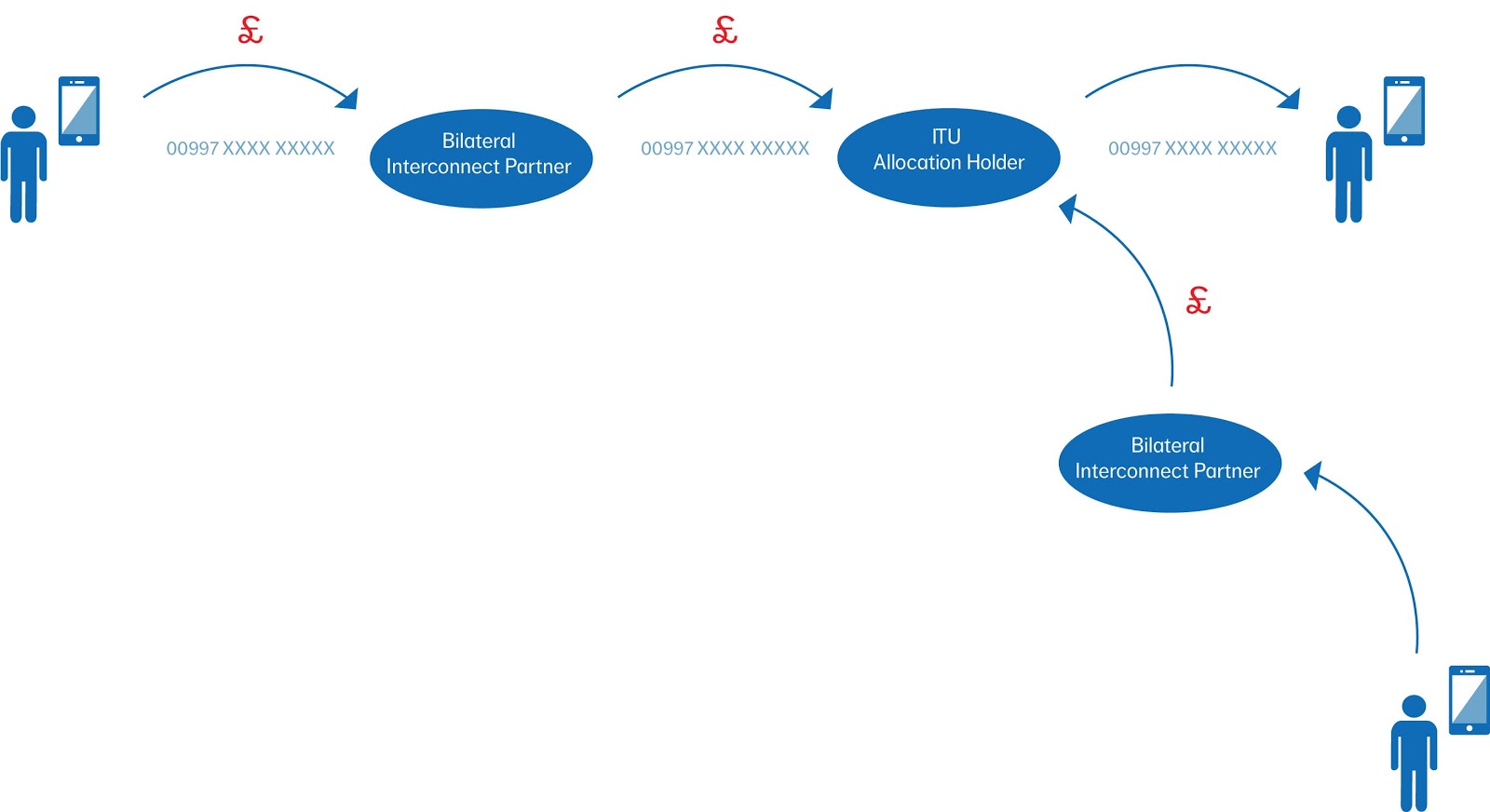
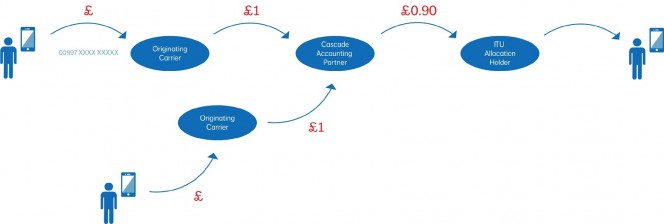
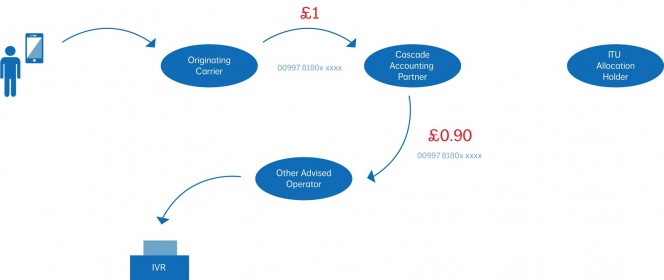
 The business mobile market is in a difficult space right now. Monthly prices are falling whilst handset costs are rising dramatically; a situation made worse in the UK where by and large we still expect to be able to get a free handset with a new contract. Of course we all know the handset is not really free, rather subsidised by the selected tariff, but the result is that many mobile providers only seeing a profit in month 18 onwards.
The business mobile market is in a difficult space right now. Monthly prices are falling whilst handset costs are rising dramatically; a situation made worse in the UK where by and large we still expect to be able to get a free handset with a new contract. Of course we all know the handset is not really free, rather subsidised by the selected tariff, but the result is that many mobile providers only seeing a profit in month 18 onwards. This all contributes to an environment where companies in the mobile space must adapt or perish. This isn’t limited to resellers, either. It can even be seen at a mobile network operator level where even the big players are beginning to move into some very untraditional services such as hosted telephony, landline services and even hosted IT products.
This all contributes to an environment where companies in the mobile space must adapt or perish. This isn’t limited to resellers, either. It can even be seen at a mobile network operator level where even the big players are beginning to move into some very untraditional services such as hosted telephony, landline services and even hosted IT products.
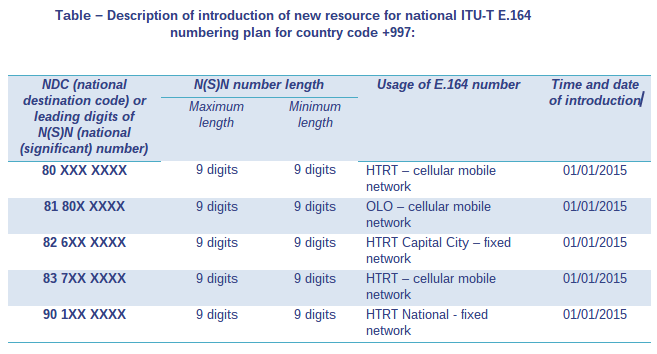
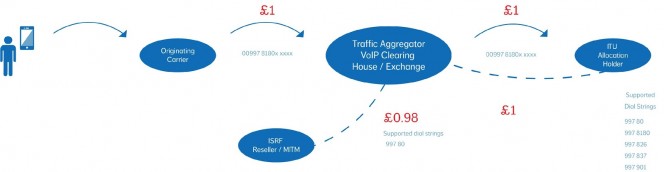
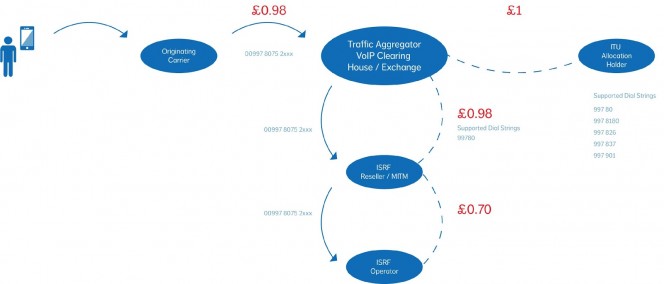
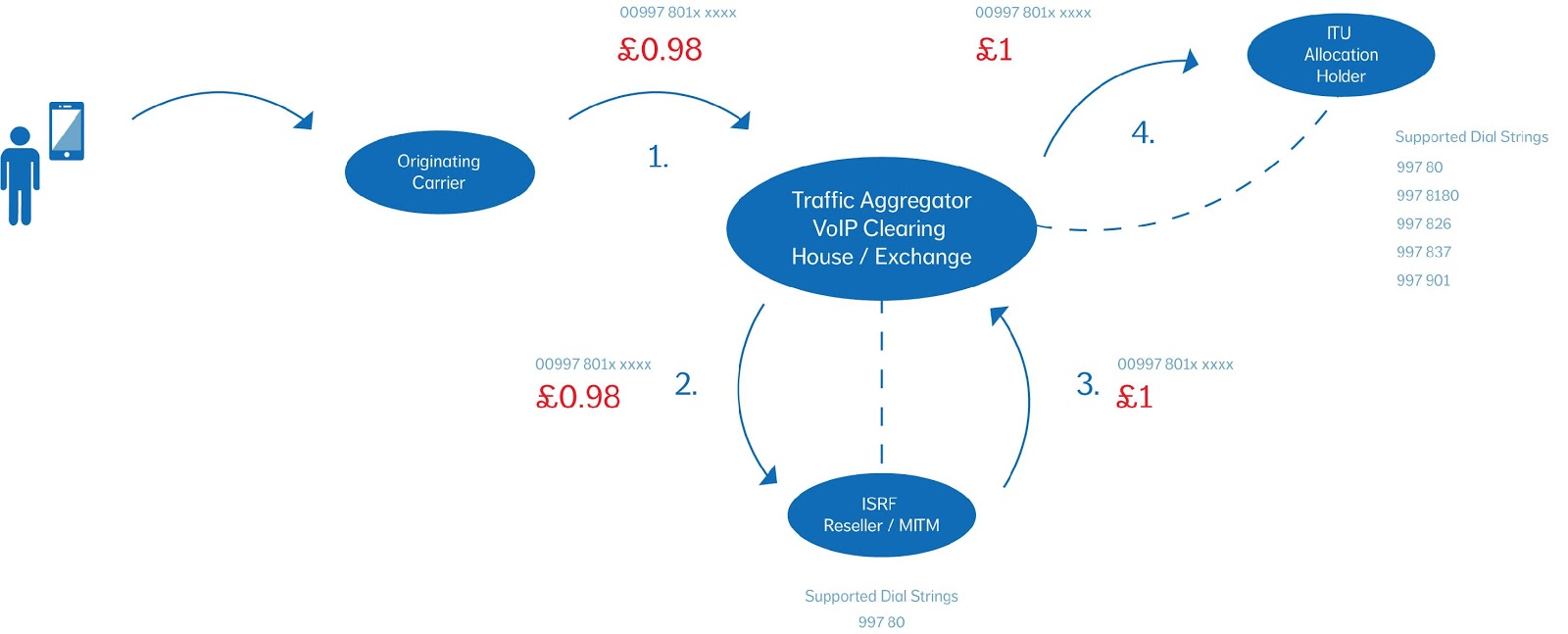

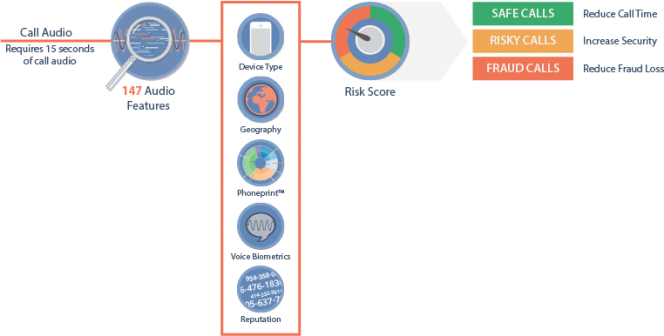




 uc executive dinner is another hit
uc executive dinner is another hit



