 Why does the Finance Director care about IP Phone Design? It’s all about IP Phone ROI
Why does the Finance Director care about IP Phone Design? It’s all about IP Phone ROI
In her sixth post this week the SNOM’s prolific Marketing Manager Lesley Hansen talks about IP Phone ROI (Return on Investment).
The best quality and most elegantly designed IP Phone in the world will not be widely accepted unless it meets business expectations regarding cost. Cost in its broadest sense will include cost of acquisition, cost of deployment, cost of ownership and return on investment. Any IP Phone design must consider each and every one of these aspects. It is because of the pressure on all businesses to meet financial targets that the Finance Director is a critical player in our considerations as we design and manufacturer each new IP handset.
Since much of the motivation for moving to IP telephony is cost related building an accurate business case, including capital, implementation, and operational costs, is crucial to selecting the best vendor and architecture for your organization.
Cost of Acquisition
There are hundreds if not thousands of IP phones on the market and they range in price from around £50 for standard phones to several thousand pounds for secure encrypted handsets for use by government employees.
Soft phones are the simplest and least expensive type of IP telephone since many are available free of charge. Soft phones work through specialised software installed directly onto a PC, laptop, or mobile phone handset. With a soft phone no handset is required, but for the comfort of the user and for improved voice quality soft phones are best used with a good quality headset or USB telephone.
One you start looking at an IP handsets at the bottom of the range you find the standard phone without many bells and whistles. Typically standard features include caller ID, limited conferencing capabilities and speed dial. As you move up in price you gain capabilities such audio capabilities and audio quality for features such as speaker phones, wider conferencing capabilities, history memory, programmable options and support for hearing aids.
Even further on you get advanced functionality such as support for voicemail and CTI options. You also gain connectivity options as the price increases, moving from a connected IP handset with an Ethernet port to ones that supports WiFi and Gigabit Ethernet, multiple Ethernet USB connections and even Bluetooth.
At the top of the range, excluding specialist phones such as the security handset already mentioned, are complex professional handsets with high quality audio provided through noise cancelling capabilities making them ideal for the busy and noisy office. Some come with programmable options for integration into your business processes as well as colour display screens with web access.
Depending on the role of the person using the IP Phone, there will be a different set of needs and each person will be looking for something different in their handset. An executive may want the latest and greatest IP Phone, while a receptionist may only be concerned with the number of total calls they can handle at one time. Most people want the standard features in a phone such as Call Waiting, Call Transfer, Call Parking and Conferencing. The items that will most effect the cost per handset are needs such as a high quality speakerphone, a large display and the capability for extra extensions.
So the selection of the right IP Phone is likely to involve a number of different handset types, a range of costs to meet the difference requirements of different employees and a degree of integration with your business functions. Doing your homework on what handsets are needed by the business is likely to save the company money in the long run. Providing handsets where the price reflects the importance of features to the business is paramount.
Cost of Deployment
Hosted VoIP is increasingly being adopted to avoid the excess costs and complexities of deployment of on-premise solutions. This is great from the end customer’s point of view as they get predictable costs. For the IP phone manufacturer it simply moves the demands for easy to deploy handset to the service provider rather than the end customer. The need is still there. The installation, provisioning and training costs for IP handset deployment varies greatly from vendor to vendor as well as from installation to installation. For example the question of how many remote deployment teams are needed and the complexity of the server/PBX installation will affect costs.
To reduce the costs of deployment Auto Provisioning can be used to provide general and specific configuration parameters (“Settings”) to the phones and to manage firmware actualization. Deployment applications enable enterprise customers and service providers to reduce deployment costs with automated remote configuration and ongoing management of the IP phones.
The Auto Provisioning application provided by Snom allows remote administration (configuration and maintenance) of an unlimited number of distinct Snom phone types. This application enables the user to unpack a Snom handset from the box, connect it to a local network and get it up and running without the need to configure anything.
The phones can be set up manually but the easiest way to provisioning the IP Handsets is to use the built-in plug and play provisioning functionality. The phone configures itself by retrieving a PBX generated phone configuration file from interoperability partners or using the phones DHCP. The provisioning manager needs to approve the handset registration and assign an extension. The server will send a provisioning link to the phone. Once the phone receives the link, it will apply the configuration on the fly, and will be ready to use. If a firmware update is needed, a restart will be performed.
Selecting handsets designed for remote provisioning is critical in the long term cost of any IP Telephony solution.
Cost of Ownership
A lot has been written about the ongoing costs of owning an IP Telephony systems. It’s tough to get accurate operational costs before actually incurring those costs, but we do know based on experience that operational costs tend to be highest during the first two years of usage of a new technology. Once staffs gain expertise from using the technology, the operational costs drop by about 20%. Reports indicate that without installing a solution offering ease of operation and remote management it is easy for a company to simply spend the money they have saved on Moves, Adds and Changes (MACs) by moving to IP Telephony on the management and monitoring of the new IP telephony system. External MACs for an old TDM environments use to cost £120 on average, and range from £50 to £200 each. IP MACs typically cost under £10 each.
The Graphical User Interface of an IP-PBX or Telephony Server will be much more user friendly than traditional PBXs. This allows for easier changes and additions. Because phones are IP based, they are like PCs, and when they are moved from one connection to another they connect right back up to the PBX server.
These offer considerable savings compared to a time when a simple phone move needed to have cross connects changed and a phone technician making a billable service call. However if the IP Handset is at a remote site and local configuration or a remote restart is needed then there can still be costs incurred. The best way to control these costs is with the selection of a handset with remote management and configuration capabilities and from a vendor who is not prone to excessive numbers of firmware updates which require handset resets or reconfiguration.
Here the recommendation is that to keep operational costs low you ensure that the phone´s interface allows remote users to simulate the usage of the phone´s keypad and special features.
IP Phone ROI
The idea of moving to IP Telephony solely to save money has slowly subsided, although it has not gone away entirely. In the early years of VOIP, companies had to find an ROI in order to justify replacing tried-and-true equipment for new technology. Now, they’re more often already in a TDM-replacement phase, so ROI becomes less important as organizations are focusing on other benefits, such as streamlined features, improved productivity, and integrated voice/data/video collaborative applications.
To be clear, there can be a net savings, and this is typically achieved after the first two years. But this net saving is easily eroded if the IP Handset selected is not suitable so that handsets have to be replaced, possibly because the wrong model for the role was selected in the first place or because the usage levels experienced in a busy office.
While the eventual costs savings for installing IP Telephony can be substantial, the start-up costs of deploying an IP telephony solution depend on a number of variables, including the size of the enterprise and the choice of vendor. To help organizations understand the total cost of ownership (TCO) of an IP telephony.
Other posts in our IP phone design week:
How to design an ip phone
How to design an ip phone for voice quality
IP phone design for it departments
IP Phone Security
IP Phone Interoperability
Check out all our VoIP posts here.
Deployment is a key contribution of the Value Added Reseller involved in the sale. Anyone interested in becoming a Snom VAR can check out their site here.

 As regular readers will know I don’t use Microsoft software anymore. I’ve suffered from so many
As regular readers will know I don’t use Microsoft software anymore. I’ve suffered from so many  Last week the license ran out. McAfee bless em wanted £59.99 for me to renew. I looked online and saw a number of deals including a lowball £25.50 but decided to nip into PC World so see what they had.
Last week the license ran out. McAfee bless em wanted £59.99 for me to renew. I looked online and saw a number of deals including a lowball £25.50 but decided to nip into PC World so see what they had. The salesman/advisor simply suggested Norton at £40 (£39.99). No problemo.
The salesman/advisor simply suggested Norton at £40 (£39.99). No problemo.


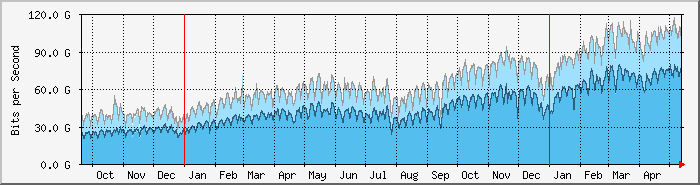
 In 19 months the traffic has almost quadrupled. It’s also interesting to note the drop off at holiday times – notably Christmas and the school summer holidays .
In 19 months the traffic has almost quadrupled. It’s also interesting to note the drop off at holiday times – notably Christmas and the school summer holidays .
 Lyndsey Burton comments on Digital Single Market
Lyndsey Burton comments on Digital Single Market
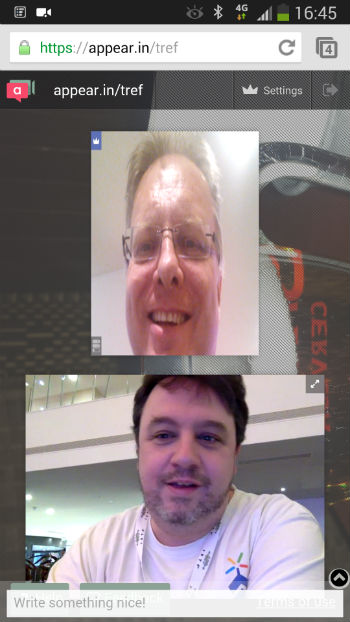

 The business mobile market is in a difficult space right now. Monthly prices are falling whilst handset costs are rising dramatically; a situation made worse in the UK where by and large we still expect to be able to get a free handset with a new contract. Of course we all know the handset is not really free, rather subsidised by the selected tariff, but the result is that many mobile providers only seeing a profit in month 18 onwards.
The business mobile market is in a difficult space right now. Monthly prices are falling whilst handset costs are rising dramatically; a situation made worse in the UK where by and large we still expect to be able to get a free handset with a new contract. Of course we all know the handset is not really free, rather subsidised by the selected tariff, but the result is that many mobile providers only seeing a profit in month 18 onwards. This all contributes to an environment where companies in the mobile space must adapt or perish. This isn’t limited to resellers, either. It can even be seen at a mobile network operator level where even the big players are beginning to move into some very untraditional services such as hosted telephony, landline services and even hosted IT products.
This all contributes to an environment where companies in the mobile space must adapt or perish. This isn’t limited to resellers, either. It can even be seen at a mobile network operator level where even the big players are beginning to move into some very untraditional services such as hosted telephony, landline services and even hosted IT products.
 If there’s a question worth asking, in 2027 there’ll be some data that supports the answer. Parties will dedicate greater spend to using big data as the foundation of each campaign – whether that’s in the capture and curation of data relevant to them or analysing it.
If there’s a question worth asking, in 2027 there’ll be some data that supports the answer. Parties will dedicate greater spend to using big data as the foundation of each campaign – whether that’s in the capture and curation of data relevant to them or analysing it. In 2027, MPs will find it much easier to balance their Parliamentary duties with those in their constituency. Technology like WebRTC will mean there’s little excuse to not participate in a debate or vote because they will be able to do so remotely, and there would no longer be the possibility for bills to be passed due to poor scheduling and low turnour. Furthermore, MPs won’t need a second home in London and can spend more time in their constituency.
In 2027, MPs will find it much easier to balance their Parliamentary duties with those in their constituency. Technology like WebRTC will mean there’s little excuse to not participate in a debate or vote because they will be able to do so remotely, and there would no longer be the possibility for bills to be passed due to poor scheduling and low turnour. Furthermore, MPs won’t need a second home in London and can spend more time in their constituency. An obvious area where technology could improve elections is in the voting process itself. For example, how backwards and archaic is it that we should turn up to a physical location with just a polling card and no verification of identity, yet we already need an online government gateway ID to get a passport? And how secure is it really to leave counts of paper ballots to volunteers? Technology like WebRTC could reduce the technical barrier of providing biomechanical verification in the process.
An obvious area where technology could improve elections is in the voting process itself. For example, how backwards and archaic is it that we should turn up to a physical location with just a polling card and no verification of identity, yet we already need an online government gateway ID to get a passport? And how secure is it really to leave counts of paper ballots to volunteers? Technology like WebRTC could reduce the technical barrier of providing biomechanical verification in the process.



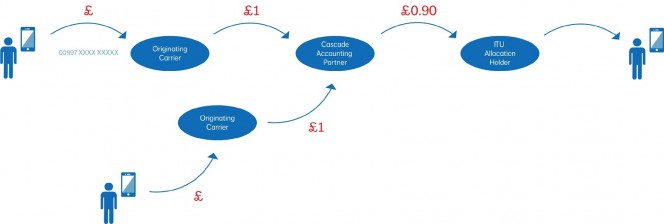
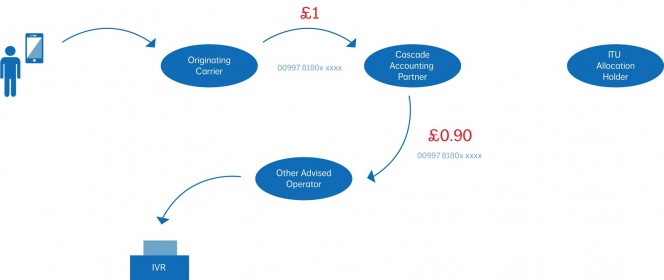
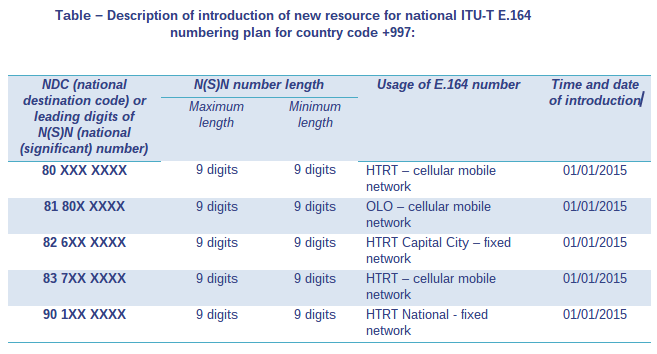
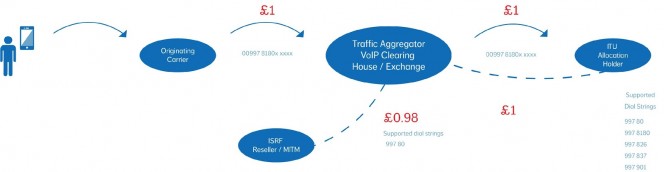
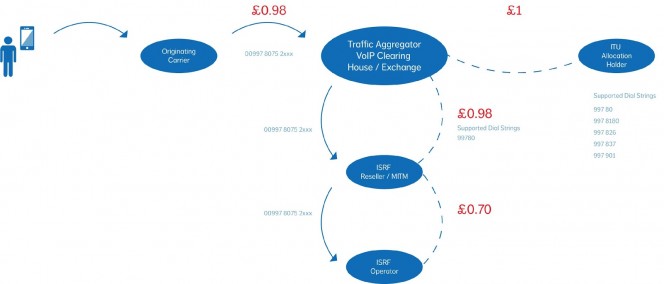
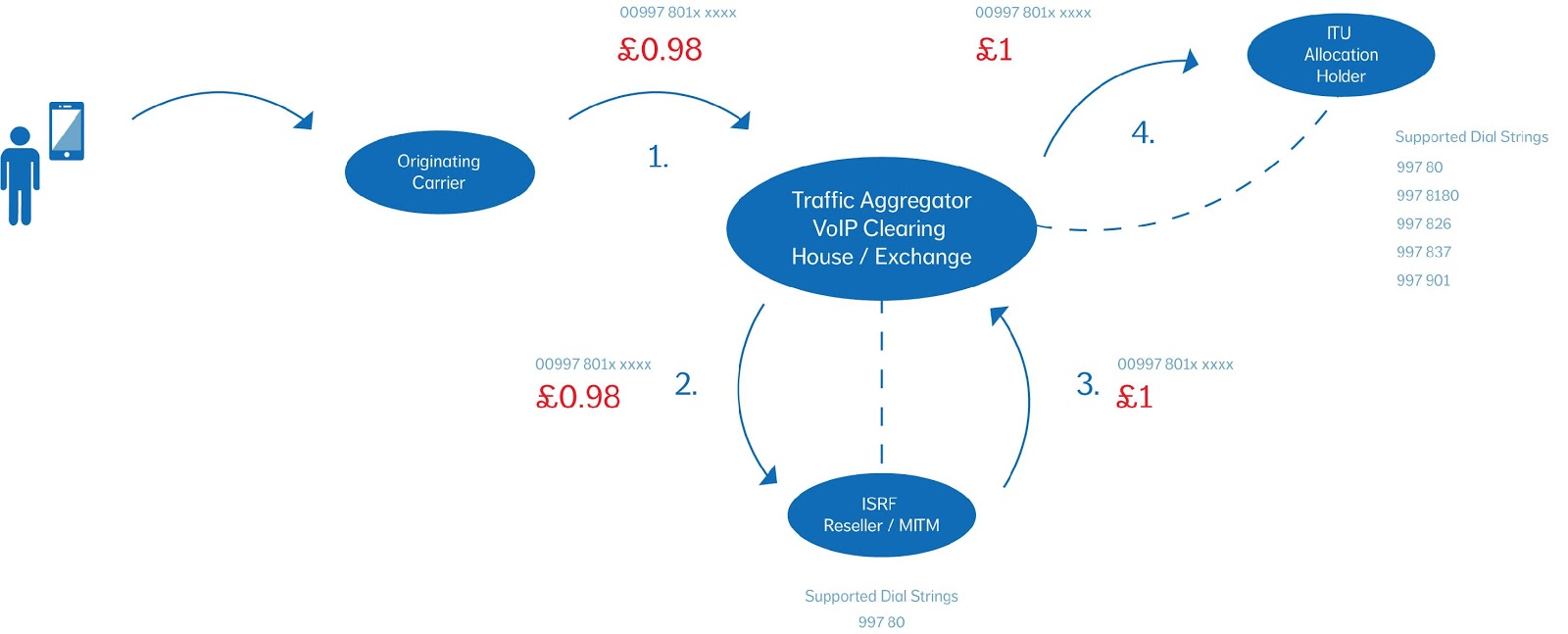






 Practical Applications for Your IP Handsets
Practical Applications for Your IP Handsets
 uc executive dinner is another hit
uc executive dinner is another hit






