VoIP has reached the mainstream. We know because the fraudsters are coming after us.
Trefor.net welcomes VoIP Week guest contributor Colin Duffy, CEO of Voipfone and ITSPA Council member.
VoIP merges two of the largest industries in the world: Telecommunications ($5.0 trillion) and the Internet ($4.2 trillion). It is big business.
Estimates of VoIP market size vary, though they are universally large. For instance, Infotenetics Research estimates the global residential and business VoIP market to be worth $64bn in 2014, growing to $88bn in 2018. Visiongain, on another hand, puts the 2018 value at $76bn. WhichVoIP (Bragg) has it as $82.7bn by 2017, and also claims that VoIP calls account for 34% of global voice traffic – 172bn call minutes. And then there is the United States Federal Communications Commission, which estimates that “In December 2011, there were 107 million end-user switched access lines in service [..in the USA and..] 37 million interconnected VoIP subscriptions.
And with opportunity comes the thief:

(You have to love that New Scotland Yard hack…..)
But it’s not confined to big organisations; perhaps a little closer to home:
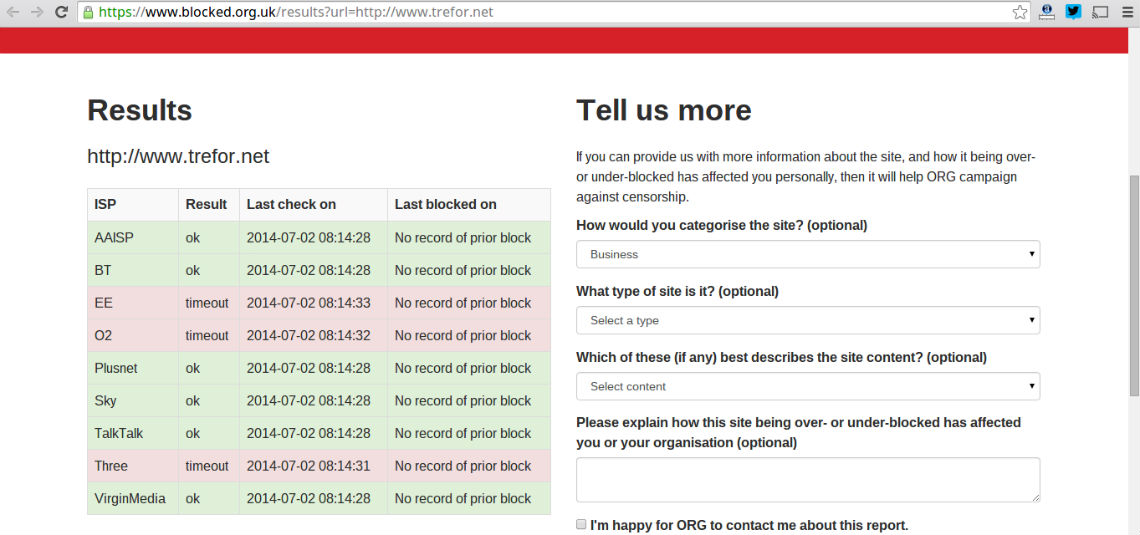
“A family-run business says it has ‘nowhere left to turn’ after hackers rigged its telephone system to call premium rate phone numbers — racking up a bill of nearly £6,000. ‘We reported it to the police, but we were told there was very little likelihood of them catching anyone so they wouldn’t be able to investigate’, she added.”
— Lancashire Telegraph
The Communications Fraud Control Association publishes a global fraud loss survey, and in 2013 they estimated that the global telecommunication industry loss to fraud was an enormous $46.3bn, which included:
- VoIP hacking ($3.6bn),
- PBX hacking ($4.4bn),
- Premium Rate Services Fraud ($4.7bn),
- Subscription Fraud ($5.2bn)
- International Revenue Share Fraud ($1.8).
Over 90% of the telephone companies included in the CFCA’s survey reported that fraud within their company had increased or stayed the same since the last report.
Globally, the top emerging fraud type was identified as Internet Revenue Sharing Fraud, with Premium Rate Service Fraud (both international and domestic) also in the top five. Of the top five emerging fraud methods, PBX Hacking was the most important with VoIP Hacking at number three.
Who’s doing all this is a big and interesting topic, but here’s a starter:
|
Top Ten Countries where fraud |
Top Ten Countries where fraud |
| *Latvia Gambia *Somalia Guinea Cuba East Timor Lithuania Taiwan *UK |
USA India *UK Brazil Philippines *Latvia Pakistan *Somalia Spain Bulgaria |
CFCA, Global Fraud Loss Survey, 2013
What can be done?
Earlier this year a customer of Voiceflex was hacked to the tune of £35,000 when over 10,000 calls were sent to a Polish Premium Service number over a period of 36 hours. The customer refused to pay, which resulted in a court case that the telco lost. Now the industry is looking to its terms and conditions for protection, but it’s clear that this isn’t enough – the cause needs addressing.
The best approach would be to cut off the money supply – if Telcos could withhold payments for known fraudulent calls, the activity would end. But this solution requires changes to inter-operator agreements and cross-jurisdiction interventions.
“We are currently in discussions with our fellow EU regulators about steps that may be taken to address cross-border [Dial Through] fraud and misuse. It is important that companies using VoIP systems take steps to ensure both the physical and technical security of their equipment in order to avoid becoming an ‘easy target’ for this type of criminal activity […..] We are approaching the NICC and relevant trade associations to ensure their advice is updated to help businesses better protect themselves against newer types of dial-through fraud that have emerged as technology has developed.”
— Ofcom 2013
For once I agree with Ofcom. The industry needs to work harder at target-hardening. We need to be making this industry safer for our customers.
There’s a lot to be done but a good start is to read and apply the guidance issued by ITSPA – the UK trade organisation for Internet Telcos.
I’m taking a close personal interest in VoIP fraud and security, and I invite anyone who has more information or who wishes to discuss this in more detail to contact me at ![]()
A naive user asked me, ‘why can’t you just make safe telephones?’ Well, why can’t we?








 The Metropolitan Line on London Underground has nice newish interconnected carriages and you can walk from one end of the train to the other. As we wound our way to Kings Cross for me to catch the train back north I noticed that the carriages were making interesting snake like movements. Very artistic I thought. I’ll video it.
The Metropolitan Line on London Underground has nice newish interconnected carriages and you can walk from one end of the train to the other. As we wound our way to Kings Cross for me to catch the train back north I noticed that the carriages were making interesting snake like movements. Very artistic I thought. I’ll video it.




